I'm an Apple guy, so I don't much worry about Windows, but this seems like a massive win. Nearly 400,000 computers worldwide have been identified as being infected with this malware. The malware shares your personal data. I run a program weekly to scan for malware, viruses, bloat, etc. I think if I had a Windows system I'd be running it daily. But if you don't do something, someone is going to get your data.

 blogs.microsoft.com
blogs.microsoft.com

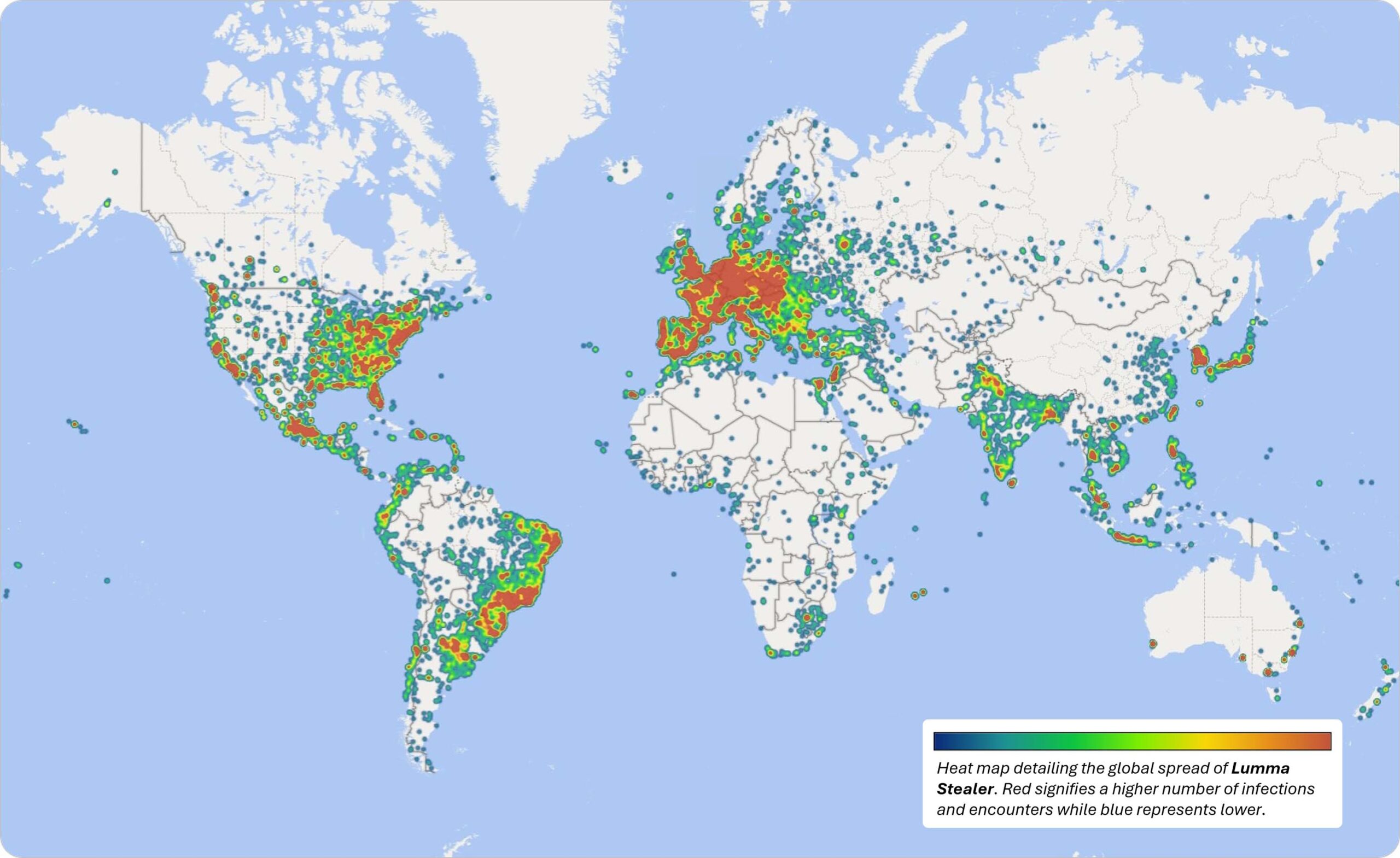 Heat map detailing global spread of Lumma Stealer malware infections and encounters across Windows devices.
Heat map detailing global spread of Lumma Stealer malware infections and encounters across Windows devices. Splash page displayed on 900+ domains seized by Microsoft.
Splash page displayed on 900+ domains seized by Microsoft.

Disrupting Lumma Stealer: Microsoft leads global action against favored cybercrime tool
Microsoft and partners disrupted Lumma Stealer, malware used to steal data and enable cybercrime. Legal action was filed on May 13 by Microsoft DCU
FULL STORY AT LINK ^^^
Disrupting Lumma Stealer: Microsoft leads global action against favored cybercrime tool
May 21, 2025

Microsoft’s Digital Crimes Unit (DCU) and international partners are disrupting the leading tool used to indiscriminately steal sensitive personal and organizational information to facilitate cybercrime. On Tuesday, May 13, Microsoft’s DCU filed a legal action against Lumma Stealer (“Lumma”), which is the favored info-stealing malware used by hundreds of cyber threat actors. Lumma steals passwords, credit cards, bank accounts, and cryptocurrency wallets and has enabled criminals to hold schools for ransom, empty bank accounts, and disrupt critical services.
Via a court order granted in the United States District Court of the Northern District of Georgia, Microsoft’s DCU seized and facilitated the takedown, suspension, and blocking of approximately 2,300 malicious domains that formed the backbone of Lumma’s infrastructure. The Department of Justice (DOJ) simultaneously seized the central command structure for Lumma and disrupted the marketplaces where the tool was sold to other cybercriminals. Europol’s European Cybercrime Center (EC3) and Japan’s Cybercrime Control Center (JC3) facilitated the suspension of locally based Lumma infrastructure.
Between March 16, 2025, and May 16, 2025, Microsoft identified over 394,000 Windows computers globally infected by the Luma malware. Working with law enforcement and industry partners, we have severed communications between the malicious tool and victims. Moreover, more than 1,300 domains seized by or transferred to Microsoft, including 300 domains actioned by law enforcement with the support of Europol, will be redirected to Microsoft sinkholes. This will allow Microsoft’s DCU to provide actionable intelligence to continue to harden the security of the company’s services and help protect online users. These insights will also assist public- and private-sector partners as they continue to track, investigate, and remediate this threat. This joint action is designed to slow the speed at which these actors can launch their attacks, minimize the effectiveness of their campaigns, and hinder their illicit profits by cutting a major revenue stream.
 Heat map detailing global spread of Lumma Stealer malware infections and encounters across Windows devices.
Heat map detailing global spread of Lumma Stealer malware infections and encounters across Windows devices. Splash page displayed on 900+ domains seized by Microsoft.
Splash page displayed on 900+ domains seized by Microsoft. What is Lumma?
Lumma is a Malware-as-a-Service (MaaS), marketed and sold through underground forums since at least 2022. Over the years, the developers released multiple versions to continually improve its capabilities. Microsoft Threat Intelligence shares more details around the delivery techniques and capabilities of Lumma in a recent blog.
Typically, the goal of Lumma operators is to monetize stolen information or conduct further exploitation for various purposes. Lumma is easy to distribute, difficult to detect, and can be programmed to bypass certain security defenses, making it a go-to tool for cybercriminals and online threat actors, including prolific ransomware actors such as Octo Tempest (Scattered Spider). The malware impersonates trusted brands, including Microsoft, and is deployed via spear-phishing emails and malvertising, among other vectors.
